In this guide, you will learn how to install GVM 21.4 on Kali Linux. Greenbone Vulnerability Management (GVM), previously known as OpenVAS, is a network security scanner which provides a set of network vulnerability tests (NVTs) to detect security loopholes in systems and applications. As of this writing, GVM 21.4.4 is the current stable release.
Install GVM 21.4 on Kali Linux
Prerequisites
In this demo, we will install and setup GVM 21.4 on Kali Linux from source code. As such, below are the system requirements I would personally recommend.
- At least 4 GB RAM
- At least 4 vCPUs
- More than 8 GB disk space (We used 16 GB in this demo)
These requirements will vary depending on your use cases, however. Just be sure to provide “enough”.
Run System Update
To begin with, update and upgrade your system packages;
apt updateCreate GVM User on Ubuntu
In this demo, we will run GVM 21.08 as a non privileged system user. Thus, create gvm system user account.
useradd -r -d /opt/gvm -c "GVM User" -s /bin/bash gvmCreate the GVM user directory as specified by option -d in the command above and set the user and group ownership to gvm.
mkdir /opt/gvm && chown gvm: /opt/gvmInstall Required Build Tools
In order to successfully build GVM 21.4 on Kali Linux, you need to install a number of required dependencies and build tools.
apt install gcc g++ make bison flex libksba-dev \
curl redis libpcap-dev cmake git pkg-config libglib2.0-dev libgpgme-dev \
nmap libgnutls28-dev uuid-dev libssh-gcrypt-dev libldap2-dev gnutls-bin \
libmicrohttpd-dev libhiredis-dev zlib1g-dev libxml2-dev libnet-dev libradcli-dev \
clang-format libldap2-dev doxygen gcc-mingw-w64 xml-twig-tools libical-dev perl-base \
heimdal-dev libpopt-dev libunistring-dev graphviz libsnmp-dev python3-setuptools \
python3-paramiko python3-lxml python3-defusedxml python3-dev gettext python3-polib \
xmltoman python3-pip texlive-fonts-recommended libpq-dev postgresql-server-dev-all \
texlive-latex-extra --no-install-recommends xsltproc sudo vim rsync -y
Install Yarn on Kali Linux
Next, install Yarn JavaScript package manager
curl -sL https://dl.yarnpkg.com/debian/pubkey.gpg | gpg --dearmor | sudo tee /usr/share/keyrings/yarnkey.gpg >/dev/nullecho "deb [signed-by=/usr/share/keyrings/yarnkey.gpg] https://dl.yarnpkg.com/debian stable main" | sudo tee /etc/apt/sources.list.d/yarn.listapt updateapt install yarn -yInstall PostgreSQL on Kali Linux
GVM 21.4 uses PostgreSQL as the backend database. We use version 14 in this setup, which is already installed on Kali Linux 2022.2 which we are using.
To check the version;
psql --versionSample output;
psql (PostgreSQL) 14.2 (Debian 14.2-1+b3)Start and enable PostgreSQL service to run on system boot;
systemctl enable --now postgresqlConfirm it is up by checking the ports opened;
ss -altnp | grep postgresLISTEN 0 244 127.0.0.1:5432 0.0.0.0:* users:(("postgres",pid=26282,fd=6))
LISTEN 0 244 [::1]:5432 [::]:* users:(("postgres",pid=26282,fd=5))Create PostgreSQL User and Database
Once the installation is done, create the PostgreSQL user and database for Greenbone Vulnerability Management Daemon (gvmd).
Note that the database and user should be created as PostgreSQL user, postgres.
sudo -Hiu postgres createuser gvmsudo -Hiu postgres createdb -O gvm gvmdGrant PostgreSQL GVM User DBA Roles
sudo -Hiu postgres psql gvmd -c 'create role dba with superuser noinherit;'sudo -Hiu postgres psql gvmd -c 'grant dba to gvm;'sudo -Hiu postgres psql gvmd -c 'create extension "uuid-ossp";'sudo -Hiu postgres psql gvmd -c 'create extension "pgcrypto";'Once that is done, restart PostgreSQL;
systemctl restart postgresqlAllow the user to run the installation with sudo rights;
echo "gvm ALL = NOPASSWD: $(which make) install" > /etc/sudoers.d/gvmBuilding GVM 21.4 from Source Code
There are different tools required to install and setup GVM 21.4 on Kali Linux. These include;
- GVM Libraries
- OpenVAS Scanner
- OSPd
- ospd-openvas
- Greenbone Vulnerability Manager
- Greenbone Security Assistant
- Python-GVM
- GVM-Tools
- OpenVAS SMB
Every component has README.md and a INSTALL.md file that explains how to build and install it.
Build and Install GVM on Kali Linux
Switch to GVM user created above and create a directory where to download the source files to;
su -Hiu gvm mkdir gvm-sourceDownload GVM 21.4 Source Files
Navigate to temporary directory created above and run the subsequent commands to clone the GVM github branch files.
sudo -Hiu gvm git clone -b stable --single-branch https://github.com/greenbone/gvm-libs.git gvm-source/gvm-libssudo -Hiu gvm git clone -b main --single-branch https://github.com/greenbone/openvas-smb.git gvm-source/openvas-smbsudo -Hiu gvm git clone -b stable --single-branch https://github.com/greenbone/openvas.git gvm-source/openvassudo -Hiu gvm git clone -b stable --single-branch https://github.com/greenbone/ospd.git gvm-source/ospdsudo -Hiu gvm git clone -b stable --single-branch https://github.com/greenbone/ospd-openvas.git gvm-source/ospd-openvassudo -Hiu gvm git clone -b stable --single-branch https://github.com/greenbone/gvmd.git gvm-source/gvmdsudo -Hiu gvm git clone -b stable --single-branch https://github.com/greenbone/gsa.git gvm-source/gsasudo -Hiu gvm git clone -b stable --single-branch https://github.com/greenbone/gsad.git gvm-source/gsadOnce the source files are in place, proceed to build and install GVM on Kali Linux.
Note the current working directory;
sudo -Hiu gvm ls -1 gvm-source
gsa
gsad
gvmd
gvm-libs
openvas
openvas-smb
ospd
ospd-openvas
To begin with, switch to GVM user account.
su - gvm
cd gvm-sourceNext, set the PKG_CONFIG_PATH environment variable to the location of your pkg-config files before configuring:
echo "export PKG_CONFIG_PATH=/opt/gvm/lib/pkgconfig:$PKG_CONFIG_PATH" >> ~/.bashrcsource ~/.bashrcBuild and Install GVM 11 Libraries
From within the source directory, /opt/gvm/gvm-source, in this setup, change to GVM libraries directory;
cd gvm-libs
mkdir build && cd build
cmake ..
make
sudo make installBuild and Install OpenVAS scanner and OpenVAS SMB
Open Vulnerability Assessment Scanner (OpenVAS) is a full-featured scan engine that executes a continuously updated and extended feed of Network Vulnerability Tests (NVTs).
OpenVAS SMB provides modules for the OpenVAS Scanner to interface with Microsoft Windows Systems through the Windows Management Instrumentation API and a winexe binary to execute processes remotely on that system.
Build and install openvas-smb;
cd ../../openvas-smb/
mkdir build && cd build
cmake ..
make
sudo make installBuild and install OpenVAS scanner;
cd ../../openvasSince Kali 2022.2 uses Glibc 2.33, you may get errors such as error: ‘g_pattern_match_string’ is deprecated: as per this issue.
Thus, disable the warnings from being treated as errors and proceed.
sed -i.bak 's/-Werror/-Wno-error/' misc/CMakeLists.txt
mkdir build && cd build
cmake ..
make
sudo make installConfiguring OpenVAS Scanner
The host scan information is stored temporarily on Redis server.
To begin run the command below to create the cache to the installed shared libraries;
exitldconfigThe default configuration of Redis server is /etc/redis/redis.conf.
Next, copy OpenVAS scanner Redis configuration file from the OpenVAS source directory, redis-openvas.conf, to the Redis config directory;
cp /opt/gvm/gvm-source/openvas/config/redis-openvas.conf /etc/redis/Update the ownership of the configuration.
chown redis:redis /etc/redis/redis-openvas.confUpdate the path to Redis unix socket on the /etc/openvas/openvas.conf using the db_address parameter.
To get the path to the Redis unix socket, run the command;
grep unixsocket /etc/redis/redis-openvas.confSample output;
unixsocket /run/redis-openvas/redis.sock
unixsocketperm 770Once you get the path to Redis unix socket, run the command;
echo "db_address = /run/redis-openvas/redis.sock" > /etc/openvas/openvas.confAdd gvm user to redis group;
usermod -aG redis gvmOptimize Redis Performance
You can also optimize Redis server itself improve the performance by making the following adjustments;
Increase the value of somaxconn in order to avoid slow clients connections issues.
echo "net.core.somaxconn = 1024" >> /etc/sysctl.confRedis background save may fail under low memory condition. To avoid this, enable memory overcommit (man 5 proc).
echo 'vm.overcommit_memory = 1' >> /etc/sysctl.confReload sysctl variables created above.
sysctl -pTo avoid creation of latencies and memory usage issues with Redis, disable Linux Kernel’s support for Transparent Huge Pages (THP). To easily work around this, create a systemd service unit for this purpose.
cat > /etc/systemd/system/disable_thp.service << 'EOL'
[Unit]
Description=Disable Kernel Support for Transparent Huge Pages (THP)
[Service]
Type=simple
ExecStart=/bin/sh -c "echo 'never' > /sys/kernel/mm/transparent_hugepage/enabled && echo 'never' > /sys/kernel/mm/transparent_hugepage/defrag"
[Install]
WantedBy=multi-user.target
EOL
Reload systemd configurations;
systemctl daemon-reloadStart and enable this service to run on system boot.
systemctl enable --now disable_thpRestart OpenVAS Redis server
systemctl enable --now redis-server@openvasConfirm the status;
systemctl status redis-server@openvas● [email protected] - Advanced key-value store (openvas)
Loaded: loaded (/lib/systemd/system/[email protected]; enabled; vendor preset: disabled)
Active: active (running) since Sat 2022-06-25 05:26:16 EDT; 5s ago
Docs: http://redis.io/documentation,
man:redis-server(1)
Main PID: 39946 (redis-server)
Status: "Ready to accept connections"
Tasks: 5 (limit: 4611)
Memory: 5.2M
CPU: 64ms
CGroup: /system.slice/system-redis\x2dserver.slice/[email protected]
└─39946 "/usr/bin/redis-server 127.0.0.1:0"
Jun 25 05:26:16 kali redis-server[39946]: `-._ `-._`-.__.-'_.-' _.-'
Jun 25 05:26:16 kali redis-server[39946]: `-._ `-.__.-' _.-'
Jun 25 05:26:16 kali redis-server[39946]: `-._ _.-'
Jun 25 05:26:16 kali redis-server[39946]: `-.__.-'
Jun 25 05:26:16 kali redis[39946]: _._
_.-``__ ''-._
_.-`` `. `_. ''-._ Redis 6.0.16 (00000000/0) 64 bit
.-`` .-```. ```\/ _.,_ ''-._
( ' , .-` | `, ) Running in standalone mode
|`-._`-...-` __...-.``-._|'` _.-'| Port: 0
| `-._ `._ / _.-' | PID: 39946
`-._ `-._ `-./ _.-' _.-'
|`-._`-._ `-.__.-' _.-'_.-'|
| `-._`-._ _.-'_.-' | http://redis.io
`-._ `-._`-.__.-'_.-' _.-'
|`-._`-._ `-.__.-' _.-'_.-'|
| `-._`-._ _.-'_.-' |
`-._ `-._`-.__.-'_.-' _.-'
`-._ `-.__.-' _.-'
`-._ _.-'
`-.__.-'
Jun 25 05:26:16 kali systemd[1]: Started Advanced key-value store (openvas).
Jun 25 05:26:16 kali redis-server[39946]: 39946:M 25 Jun 2022 05:26:16.258 # Server initialized
Jun 25 05:26:16 kali redis-server[39946]: 39946:M 25 Jun 2022 05:26:16.259 * The server is now ready to accept connections at /run/redis-openvas/redis.sock
Jun 25 05:26:16 kali redis[39946]: Server initialized
Jun 25 05:26:16 kali redis[39946]: The server is now ready to accept connections at /run/redis-openvas/redis.sock
Update Network Vulnerability Tests (NVTs)
Update Network Vulnerability Tests feed from Greenbone Security Feed/Community Feed using the greenbone-nvt-sync command. rsync tool is required for a successful synchronization.
Note that greenbone-nvt-sync must not be executed as privileged user root. For this reason, update the NVTs as gvm user created above.
Ensure that user can write to OpenVAS libraries directory, /var/lib/openvas/, directory.
chown -R gvm: /var/lib/openvas/Also, allow GVM user to run openvas with sudo rights.
echo "gvm ALL = NOPASSWD: $(which openvas)" >> /etc/sudoers.d/gvmNext, update the NVTs GVM user;
sudo -Hiu gvm greenbone-nvt-syncIf the command fails with:
rsync: [receiver] read error: Connection reset by peer (104)
rsync error: error in socket IO (code 10) at io.c(784) [receiver=3.2.3]
rsync: connection unexpectedly closed (1913648 bytes received so far) [generator]
rsync error: error in rsync protocol data stream (code 12) at io.c(228) [generator=3.2.3]Then append --rsync option and rerun the command.
sudo -Hiu gvm greenbone-nvt-sync --rsyncOnce the update is done, you need to upload the plugins into Redis server;
sudo -Hiu gvm sudo openvas --update-vt-infoBuild and Install Greenbone Vulnerability Manager
su - gvmcd gvm-source/gvmd
source ~/.bashrc
sed -i.bak 's/-Werror/-Wno-error/' CMakeLists.txt
mkdir build && cd build
cmake .. -DPostgreSQL_TYPE_INCLUDE_DIR=/usr/include/postgresql/
make
sudo make installBuild and Install Greenbone Security Assistant
The Greenbone Security Assistant is the web interface developed for the Greenbone Security Manager
cd ../../gsa
rm -rf build
yarn
yarn buildAll content of the production build can be shipped with every web server. For providing GSA via gsad web server, the files need to be copied into the /usr/local/share/gvm/gsad/web/.
Build and Install Greenbone Security Assistant HTTP server
The Greenbone Security Assistant HTTP Server is the server developed for the communication with the Greenbone Security Manager appliances. It connects to the Greenbone Vulnerability Manager Daemon gvmd to provide a full-featured user interface for vulnerability management.
cd ../gsad
mkdir build && cd build
cmake ..
make
sudo make installNext, copy the web interface configs;
exit[[ -d /usr/local/share/gvm/gsad/web ]] || mkdir -p /usr/local/share/gvm/gsad/webcp -rp /opt/gvm/gvm-source/gsa/build/* /usr/local/share/gvm/gsad/webchown -R gvm: /usr/local/share/gvm/gsad/webKeeping the feeds up-to-date
The gvmd Data, SCAP and CERT Feeds should be kept up-to-date by calling the greenbone-feed-sync script regularly (e.g. via a cron entry):
chown -R gvm: /var/lib/gvm/sudo -Hiu gvm greenbone-feed-sync --type GVMD_DATAsudo -Hiu gvm greenbone-feed-sync --type SCAPsudo -Hiu gvm greenbone-feed-sync --type CERTPlease note: The CERT feed sync depends on data provided by the SCAP feed and should be called after syncing the later.
Also, in case the commands fail with such an error;
rsync: read error: Connection reset by peer (104)
rsync error: error in socket IO (code 10) at io.c(794) [receiver=3.1.3]
rsync: connection unexpectedly closed (1047 bytes received so far) [generator]
rsync error: error in rsync protocol data stream (code 12) at io.c(235) [generator=3.1.3]Try adding --rsync option to the command, for example;
sudo -u gvm greenbone-feed-sync --type CERT --rsyncConsider setting cron jobs to run the nvts, cert and scap data update scripts at your preferred frequency to pull updates from the feed servers.
Generate GVM Certificates
Next, run the command below to generate certificates gvmd.
Server certificates are used for authentication while client certificates are primarily used for authorization. More on man gvm-manage-certs.
sudo -Hiu gvm gvm-manage-certs -aBuild and Install OSPd and OSPd-OpenVAS
Open Scanner Protocol (OSP) creates a unified interface for different security scanners and makes their control flow and scan results consistently available under the central Greenbone Vulnerability Manager service.
su - gvmsource ~/.bashrcpip3 install wheel
pip3 install python-gvm gvm-toolscd /opt/gvm/gvm-source/ospd
python3 -m pip install ospdcd /opt/gvm/gvm-source/ospd-openvas
python3 -m pip install .Once done, exit.
exitUpdate the PATH environment variable with /opt/gvm/.local/bin.
sed -i.bak '/^PATH/s#$#:/opt/gvm/.local/bin#' /etc/environmentsource /etc/environmentRunning OpenVAS Scanner, GSA and GVM services
In order to make the management of OpenVAS scanner, GSA (WebUI service) and GVM daemon, create systemd service unit files for each of them as follows.
Create OpenVAS systemd service
cat > /etc/systemd/system/ospd-openvas.service << 'EOL'
[Unit]
Description=OSPd Wrapper for the OpenVAS Scanner (ospd-openvas)
After=network.target networking.service [email protected] postgresql.service
[email protected]
ConditionKernelCommandLine=!recovery
[Service]
ExecStartPre=-rm -rf /run/gvm/ospd-openvas.pid /run/gvm/ospd-openvas.sock
Type=simple
User=gvm
Group=gvm
RuntimeDirectory=gvm
Environment=PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/opt/gvm/.local/bin
ExecStart=/opt/gvm/.local/bin/ospd-openvas \
--pid-file /run/gvm/ospd-openvas.pid \
--log-file /var/log/gvm/ospd-openvas.log \
--lock-file-dir /run/gvm -u /run/gvm/ospd-openvas.sock
RemainAfterExit=yes
[Install]
WantedBy=multi-user.target
EOL
Set proper ownership for logs directory, /var/log/gvm and run time data directory, /run/gvm;
chown -R gvm: /var/log/gvm /run/gvm/Reload systemd service unit configurations.
systemctl daemon-reloadsystemctl start ospd-openvasCheck the status of the service;
systemctl status ospd-openvas
● ospd-openvas.service - OSPd Wrapper for the OpenVAS Scanner (ospd-openvas)
Loaded: loaded (/etc/systemd/system/ospd-openvas.service; disabled; vendor preset: disabled)
Active: active (exited) since Sun 2022-06-26 15:31:01 EDT; 6s ago
Process: 97434 ExecStartPre=rm -rf /run/gvm/ospd-openvas.pid /run/gvm/ospd-openvas.sock (code=exited, status=0/SUCCESS)
Process: 97435 ExecStart=/opt/gvm/.local/bin/ospd-openvas --pid-file /run/gvm/ospd-openvas.pid --log-file /var/log/gvm/ospd-openvas.log --lock-file-dir /run/gvm -u /run/gvm/ospd-openvas.sock (code=exited, status=0/SUCCESS)
Main PID: 97435 (code=exited, status=0/SUCCESS)
Tasks: 4 (limit: 4611)
Memory: 23.4M
CPU: 535ms
CGroup: /system.slice/ospd-openvas.service
├─97442 /usr/bin/python3 /opt/gvm/.local/bin/ospd-openvas --pid-file /run/gvm/ospd-openvas.pid --log-file /var/log/gvm/ospd-openvas.log --lock-file-dir /run/gvm -u /run/gvm/ospd-openvas.sock
└─97444 /usr/bin/python3 /opt/gvm/.local/bin/ospd-openvas --pid-file /run/gvm/ospd-openvas.pid --log-file /var/log/gvm/ospd-openvas.log --lock-file-dir /run/gvm -u /run/gvm/ospd-openvas.sock
Jun 26 15:31:01 kali systemd[1]: Starting OSPd Wrapper for the OpenVAS Scanner (ospd-openvas)...
Jun 26 15:31:01 kali systemd[1]: Started OSPd Wrapper for the OpenVAS Scanner (ospd-openvas).
Enable OpenVAS scanner to run on system boot;
systemctl enable ospd-openvasCheck the logs on;
tail -f /var/log/gvm/ospd-openvas.logCreating Systemd Service units for GVM services
When run, the installer creates GVM daemon service unit, /lib/systemd/system/gvmd.service.
Let us modify this service unit file;
cp /lib/systemd/system/gvmd.service{,.bak}
cat > /lib/systemd/system/gvmd.service << 'EOL'
[Unit]
Description=Greenbone Vulnerability Manager daemon (gvmd)
After=network.target networking.service postgresql.service ospd-openvas.service
Wants=postgresql.service ospd-openvas.service
Documentation=man:gvmd(8)
ConditionKernelCommandLine=!recovery
[Service]
Type=forking
User=gvm
Group=gvm
RuntimeDirectory=gvmd
Environment=PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/opt/gvm/.local/bin
ExecStart=/usr/local/sbin/gvmd --osp-vt-update=/run/gvm/ospd-openvas.sock
Restart=always
TimeoutStopSec=10
[Install]
WantedBy=multi-user.target
EOL
Reload system unit configs and start the services;
systemctl daemon-reload
systemctl enable --now gvmdChecking the status;
systemctl status gvmd
● gvmd.service - Greenbone Vulnerability Manager daemon (gvmd)
Loaded: loaded (/lib/systemd/system/gvmd.service; enabled; vendor preset: disabled)
Active: active (running) since Sun 2022-06-26 15:32:27 EDT; 6s ago
Docs: man:gvmd(8)
Process: 97899 ExecStart=/usr/local/sbin/gvmd --osp-vt-update=/run/gvm/ospd-openvas.sock (code=exited, status=0/SUCCESS)
Main PID: 97904 (gvmd)
Tasks: 1 (limit: 4611)
Memory: 5.3M
CPU: 84ms
CGroup: /system.slice/gvmd.service
└─97904 "gvmd: Initializing"
Jun 26 15:32:26 kali systemd[1]: Starting Greenbone Vulnerability Manager daemon (gvmd)...
Jun 26 15:32:27 kali systemd[1]: Started Greenbone Vulnerability Manager daemon (gvmd).
Check the logs;
tail -f /var/log/gvm/gvmd.logCreating Systemd Service units for GSA services
When run, the installer creates GSA daemon service unit, /lib/systemd/system/gsad.service.
Let us modify this service unit file;
cp /lib/systemd/system/gsad.service{,.bak}
cat > /lib/systemd/system/gsad.service << 'EOL'
[Unit]
Description=Greenbone Security Assistant daemon (gsad)
Documentation=man:gsad(8) https://www.greenbone.net
After=network.target gvmd.service
Wants=gvmd.service
[Service]
Type=simple
User=gvm
Group=gvm
RuntimeDirectory=gsad
PIDFile=/run/gsad/gsad.pid
Environment=PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/opt/gvm/.local/bin
ExecStart=/usr/bin/sudo /usr/local/sbin/gsad -k /var/lib/gvm/private/CA/clientkey.pem -c /var/lib/gvm/CA/clientcert.pem
RemainAfterExit=yes
[Install]
WantedBy=multi-user.target
EOL
The option, -k /var/lib/gvm/private/CA/clientkey.pem -c /var/lib/gvm/CA/clientcert.pem, is as per the certificates path generated by running the gvm-manage-certs command above.
Enable GVM user to run gsad with sudo rights;
echo "gvm ALL = NOPASSWD: $(which gsad)" >> /etc/sudoers.d/gvmReload system unit configs and start the services;
systemctl daemon-reload
systemctl enable --now gsadChecking the status;
systemctl status gsad
● gsad.service - Greenbone Security Assistant daemon (gsad)
Loaded: loaded (/lib/systemd/system/gsad.service; enabled; vendor preset: disabled)
Active: active (running) since Sun 2022-06-26 15:38:53 EDT; 16s ago
Docs: man:gsad(8)
https://www.greenbone.net
Main PID: 99854 (gsad)
Tasks: 4 (limit: 4611)
Memory: 3.0M
CPU: 52ms
CGroup: /system.slice/gsad.service
├─99853 /usr/local/sbin/gsad -k /var/lib/gvm/private/CA/clientkey.pem -c /var/lib/gvm/CA/clientcert.pem
└─99854 /usr/local/sbin/gsad -k /var/lib/gvm/private/CA/clientkey.pem -c /var/lib/gvm/CA/clientcert.pem
Jun 26 15:38:53 kali systemd[1]: Started Greenbone Security Assistant daemon (gsad).
Jun 26 15:38:53 kali sudo[99850]: gvm : PWD=/ ; USER=root ; COMMAND=/usr/local/sbin/gsad -k /var/lib/gvm/private/CA/clientkey.pem -c /var/lib/gvm/CA/clientcert.pem
Jun 26 15:38:53 kali sudo[99850]: pam_unix(sudo:session): session opened for user root(uid=0) by (uid=998)
Jun 26 15:38:54 kali sudo[99852]: Oops, secure memory pool already initialized
Jun 26 15:38:54 kali sudo[99850]: pam_unix(sudo:session): session closed for user root
Check the logs;
tail -f /var/log/gvm/gsad.logCreate GVM Scanner
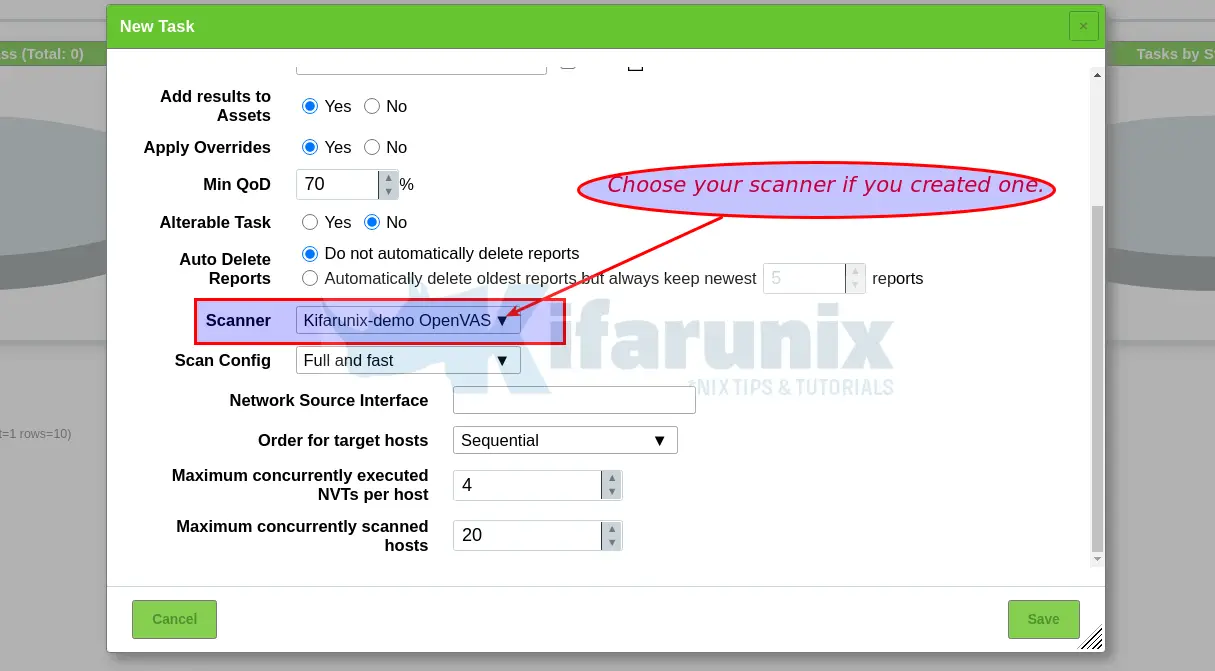
Since we launched the scanner and set it to use our non-standard scanner host path (/var/run/gvm/ospd-openvas.sock), we need to create and register our scanner;
sudo -Hiu gvm gvmd --create-scanner="Kifarunix-demo OpenVAS Scanner" \
--scanner-type="OpenVAS" --scanner-host=/run/gvm/ospd-openvas.sockcommand output;
Scanner created.Next, you need to verify your scanner. For this, you first need to get the scanner identifier;
sudo -Hiu gvm gvmd --get-scanners08b69003-5fc2-4037-a479-93b440211c73 OpenVAS /run/ospd/ospd-openvas.sock 0 OpenVAS Default
6acd0832-df90-11e4-b9d5-28d24461215b CVE 0 CVE
0d0584a1-9b12-49fb-8a46-2ece4291387c OpenVAS /run/gvm/ospd-openvas.sock 9390 Kifarunix-demo OpenVAS ScannerBased on the output above, our scanner UUID is, 0d0584a1-9b12-49fb-8a46-2ece4291387c.
Verify the scanner;
sudo -Hiu gvm gvmd --verify-scanner=0d0584a1-9b12-49fb-8a46-2ece4291387cCommand output;
Scanner version: OpenVAS 21.4.5~dev1~git-be09f30d-stable.Create GVM Admin User
Create GVM administrative user by running the command below;
sudo -Hiu gvm gvmd --create-user adminThis command generates a random password for the user. See sample output below;
User created with password 'e1a0bf5d-71b7-4e74-8e44-1acd1f9b6ddf'.If you want to create a user and at the same time create your own password;
sudo -Hiu gvm gvmd --create-user USERNAME --password=PASSWORDOtherwise, you can reset the password of an already existing user;
sudo -Hiu gvm gvmd --user=<USERNAME> --new-password=<PASSWORD>An administrator user can later create further users or administrators via clients like the Greenbone Security Assistant (GSA).
Set the Feed Import Owner
According to gvmd/INSTALL.md, certain resources that were previously part of the gvmd source code are now shipped via the feed. An example is the config “Full and Fast”.
gvmd will only create these resources if a “Feed Import Owner” is configured:
sudo -Hiu gvm gvmd --modify-setting 78eceaec-3385-11ea-b237-28d24461215b --value <uuid_of_user>The UUIDs of all created users can be found using
sudo -Hiu gvm gvmd --get-users --verboseSample output;
admin bd93f503-264e-4212-89d0-468942eba39cThen modify the gvmd settings with the user UUID.
sudo -Hiu gvm gvmd --modify-setting 78eceaec-3385-11ea-b237-28d24461215b --value bd93f503-264e-4212-89d0-468942eba39cAccessing GVM 21.04 Web Interface
Greenbone Security Assistant (GSA) WebUI daemon opens port 443 and listens on all interfaces.
ss -altnp | grep 443LISTEN 0 1024 *:443 *:* users:(("gsad",pid=99853,fd=10))If firewall is running, open this port to allow external access.
ufw allow 443/tcpYou can now access GSA via the url https:<serverIP-OR-hostname>.
Accept the self-signed SSL warning and proceed.
Login with the administrative credentials generated above.
SecInfo.
Note that it may take sometime to update the database with SCAP data and you may see No SCAP database found on the dashboard. Be sure to check the logs to confirm that actually the database is being updated;
tail -f /var/log/gvm/gvmd.log
md manage:MESSAGE:2022-06-26 19h42.57 utc:101056: No SCAP database found
md main:MESSAGE:2022-06-26 19h43.44 utc:101274: Greenbone Vulnerability Manager version 21.4.6~dev1~git-500ef0c5-stable (GIT revision 500ef0c5-stable) (DB revision 242)
md manage: INFO:2022-06-26 19h43.44 utc:101274: Getting users.
md manage:MESSAGE:2022-06-26 19h43.44 utc:101274: No SCAP database found
md main:MESSAGE:2022-06-26 19h44.36 utc:101508: Greenbone Vulnerability Manager version 21.4.6~dev1~git-500ef0c5-stable (GIT revision 500ef0c5-stable) (DB revision 242)
md manage: INFO:2022-06-26 19h44.36 utc:101508: Modifying setting.
md manage:MESSAGE:2022-06-26 19h44.36 utc:101508: No SCAP database found
md manage: INFO:2022-06-26 19h46.37 UTC:98768: Updating /var/lib/gvm/scap-data/nvdcve-2.0-2002.xml
md manage: INFO:2022-06-26 19h47.48 UTC:98768: Updating /var/lib/gvm/scap-data/nvdcve-2.0-2012.xml
md manage: INFO:2022-06-26 19h49.16 UTC:98768: Updating /var/lib/gvm/scap-data/nvdcve-2.0-2009.xml
md manage: INFO:2022-06-26 19h50.35 UTC:98768: Updating /var/lib/gvm/scap-data/nvdcve-2.0-2017.xml
md manage: INFO:2022-06-26 19h53.45 UTC:98768: Updating /var/lib/gvm/scap-data/nvdcve-2.0-2005.xml
md manage: INFO:2022-06-26 19h54.48 UTC:98768: Updating /var/lib/gvm/scap-data/nvdcve-2.0-2011.xml
md manage: INFO:2022-06-26 19h55.34 UTC:98768: Updating /var/lib/gvm/scap-data/nvdcve-2.0-2006.xml
md manage: INFO:2022-06-26 19h56.13 UTC:98768: Updating /var/lib/gvm/scap-data/nvdcve-2.0-2022.xml
md manage: INFO:2022-06-26 19h57.37 UTC:98768: Updating /var/lib/gvm/scap-data/nvdcve-2.0-2014.xml
md manage: INFO:2022-06-26 19h58.39 UTC:98768: Updating /var/lib/gvm/scap-data/nvdcve-2.0-2013.xml
md manage: INFO:2022-06-26 19h59.31 UTC:98768: Updating /var/lib/gvm/scap-data/nvdcve-2.0-2021.xml
md manage: INFO:2022-06-26 20h04.11 UTC:98768: Updating /var/lib/gvm/scap-data/nvdcve-2.0-2020.xml
md manage: INFO:2022-06-26 20h06.45 UTC:98768: Updating /var/lib/gvm/scap-data/nvdcve-2.0-2008.xml
md manage: INFO:2022-06-26 20h08.45 UTC:98768: Updating /var/lib/gvm/scap-data/nvdcve-2.0-2007.xml
md manage: INFO:2022-06-26 20h09.40 UTC:98768: Updating /var/lib/gvm/scap-data/nvdcve-2.0-2018.xml
md manage: INFO:2022-06-26 20h11.42 UTC:98768: Updating /var/lib/gvm/scap-data/nvdcve-2.0-2003.xml
md manage: INFO:2022-06-26 20h11.53 UTC:98768: Updating /var/lib/gvm/scap-data/nvdcve-2.0-2004.xml
md manage: INFO:2022-06-26 20h12.10 UTC:98768: Updating /var/lib/gvm/scap-data/nvdcve-2.0-2016.xml
md manage: INFO:2022-06-26 20h12.56 UTC:98768: Updating /var/lib/gvm/scap-data/nvdcve-2.0-2010.xml
md manage: INFO:2022-06-26 20h13.34 UTC:98768: Updating OVAL data
md manage: INFO:2022-06-26 20h13.45 UTC:98768: Updating /var/lib/gvm/scap-data/oval/5.10/org.mitre.oval/c/oval.xml
md manage: INFO:2022-06-26 20h13.45 UTC:98768: Updating /var/lib/gvm/scap-data/oval/5.10/org.mitre.oval/i/oval.xml
md manage: INFO:2022-06-26 20h13.46 UTC:98768: Updating /var/lib/gvm/scap-data/oval/5.10/org.mitre.oval/m/oval.xml
md manage: INFO:2022-06-26 20h13.47 UTC:98768: Updating /var/lib/gvm/scap-data/oval/5.10/org.mitre.oval/p/oval.xml
md manage: INFO:2022-06-26 20h14.42 UTC:98768: Updating /var/lib/gvm/scap-data/oval/5.10/org.mitre.oval/v/family/ios.xml
md manage: INFO:2022-06-26 20h14.44 UTC:98768: Updating /var/lib/gvm/scap-data/oval/5.10/org.mitre.oval/v/family/macos.xml
md manage: INFO:2022-06-26 20h14.45 UTC:98768: Updating /var/lib/gvm/scap-data/oval/5.10/org.mitre.oval/v/family/pixos.xml
md manage: INFO:2022-06-26 20h14.45 UTC:98768: Updating /var/lib/gvm/scap-data/oval/5.10/org.mitre.oval/v/family/unix.xml
md manage: INFO:2022-06-26 20h14.50 UTC:98768: Updating /var/lib/gvm/scap-data/oval/5.10/org.mitre.oval/v/family/windows.xml
md manage: INFO:2022-06-26 20h14.55 UTC:98768: Updating user OVAL definitions.
md manage: INFO:2022-06-26 20h14.55 UTC:98768: Updating CVSS scores and CVE counts for CPEs
md manage: INFO:2022-06-26 20h47.02 UTC:98768: Updating CVSS scores for OVAL definitions
md manage: INFO:2022-06-26 20h47.26 UTC:98768: Updating placeholder CPEs
md manage: INFO:2022-06-26 21h07.52 UTC:98768: Updating Max CVSS for DFN-CERT
md manage: INFO:2022-06-26 21h10.31 UTC:98768: Updating DFN-CERT CVSS max succeeded.
md manage: INFO:2022-06-26 21h10.31 UTC:98768: Updating Max CVSS for CERT-Bund
md manage: INFO:2022-06-26 21h10.40 UTC:98768: Updating CERT-Bund CVSS max succeeded.
md manage: INFO:2022-06-26 21h11.28 UTC:98768: update_scap_end: Updating SCAP info succeeded
md manage: INFO:2022-06-26 21h11.47 UTC:124270: OSP service has different VT status (version 202206240940) from database (version (null), 0 VTs). Starting update ...
md manage: INFO:2022-06-26 21h21.35 UTC:124270: Updating VTs in database ... 99743 new VTs, 0 changed VTs
md manage: INFO:2022-06-26 21h22.48 UTC:124270: Updating VTs in database ... done (99743 VTs).
...
And there you go. That is all it take to install and Setup GVM 21.4.4 on Kali Linux 2022.2. You can now start running your scans.
NOTE: When creating a scan task, be sure to select the Scanner we created above.
You can now create your target hosts to scan and schedule the scans to run at your own preferred time.
That marks the end of our tutorial on how to install GVM on Kali Linux.